Introduction
Trezor.io/start is the official onboarding portal for users who want to set up their Trezor hardware wallet securely and correctly. Hardware wallets remain one of the safest ways to store cryptocurrencies because they keep private keys offline, away from internet-connected devices. In an environment where cyberattacks, scams, and malware constantly evolve, relying on a dedicated physical device gives users a significant advantage in protecting their assets. Trezor wallets, developed by SatoshiLabs, have been pioneers in this space and continue to be trusted by millions around the world. This guide explores how the setup works, why Trezor remains a trusted solution, and how users can maintain strong security habits throughout their crypto journey.
Whether you are new to cryptocurrencies or an experienced investor, understanding the onboarding process helps avoid mistakes that could expose your funds. Trezor devices are designed to be intuitive while still offering strong cryptographic protection. By completing each step carefully and understanding the device’s security model, users gain confidence and long-term control over their digital assets.
The Security Philosophy Behind Trezor
Trezor wallets use a secure microcontroller that isolates private keys from the computer or smartphone used to manage transactions. Because the keys never leave the device, even a compromised computer cannot access them. Every transaction must be verified manually on the device screen, which prevents unauthorized transfers and ensures the user always knows what is being signed.
Transparency is another core principle of the Trezor ecosystem. The firmware is open source, meaning security researchers and independent developers can inspect and audit the code. This openness helps identify vulnerabilities early and strengthens confidence in the system. Over time, this approach has made Trezor one of the most reputable hardware wallets in the industry.
Preparing Your Device for Setup
Before powering on the device, users should confirm that the packaging is intact and shows no signs of tampering. A compromised device cannot be trusted because attackers may attempt to modify hardware before it reaches the customer. If anything appears suspicious, the safest action is to stop the setup and contact the retailer or manufacturer.
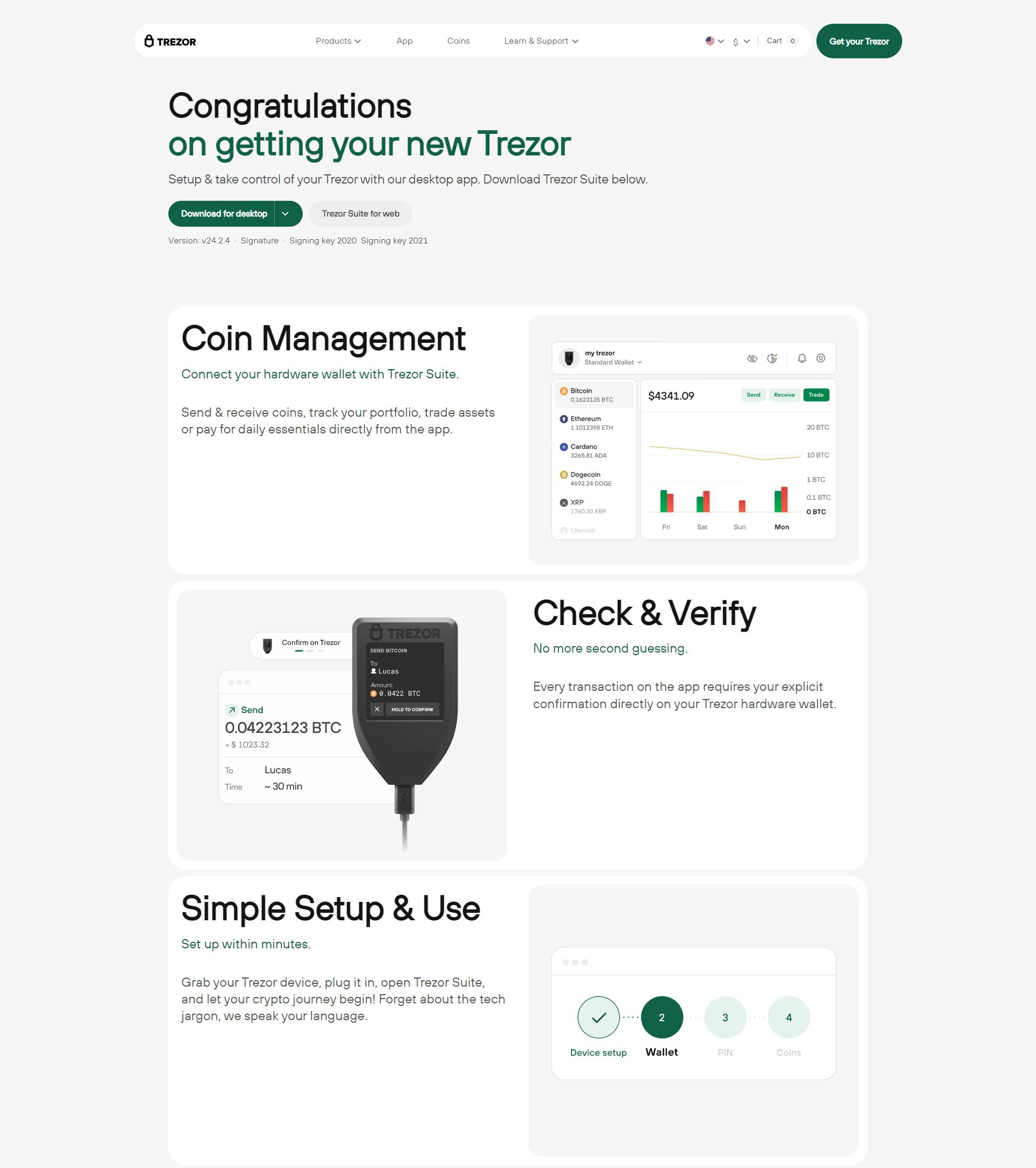
Once authenticity is confirmed, you should visit the official onboarding portal and download Trezor Suite. Trezor Suite acts as a companion application that helps initialize the device, manage accounts, update firmware, and interact with supported cryptocurrencies. Its interface is clean and beginner-friendly, guiding users through each step with clear instructions.
Initializing Your Trezor Wallet
During initialization, the device prompts you to set a PIN code. The PIN protects access to the wallet interface and prevents unauthorized individuals from using the device if it is lost or stolen. After choosing a PIN, the device generates a recovery seed composed of 12 or 24 words. This seed is the master backup for your wallet, and it must be written down accurately.
The recovery seed is extremely sensitive because anyone who possesses it can restore your wallet and access your funds. Therefore, it should always be stored offline, preferably on a metal backup plate designed to resist environmental damage. Digital storage—such as photographs, cloud backups, or notes apps—should never be used because it introduces unnecessary risk.
Managing Cryptocurrencies with Trezor Suite
Once the device is initialized, Trezor Suite allows you to add accounts, view balances, and perform transactions. The software supports a wide range of currencies, and new assets are continually added as the ecosystem expands. Each transaction still requires physical confirmation on the device, maintaining a secure workflow even when the connected computer is untrusted.
Trezor Suite also offers portfolio views, transaction history, and integration with third-party services. Advanced users benefit from features such as passphrase support, while beginners enjoy a simple and safe interface. No matter the complexity, the private keys always remain stored inside the hardware wallet, never exposed to external software.
Maintaining Long-Term Security
Security does not end after setup. Users must continue practicing safe habits such as never sharing the recovery seed, avoiding suspicious links, and ensuring firmware updates are installed regularly. Phishing attacks often imitate official websites, so always double-check URLs before downloading anything. Trezor.io/start is the only legitimate entry point for the setup process.
Conclusion
Trezor hardware wallets provide a dependable and user-controlled method for storing cryptocurrencies safely. By keeping private keys offline, requiring physical verification for transactions, and embracing a transparent open-source model, Trezor remains a trusted tool for self-custody. Proper setup, careful storage of the recovery seed, and consistent security practices ensure long-term protection. As digital assets continue to grow in importance, reliable hardware wallets like Trezor play a crucial role in safeguarding financial autonomy and reducing exposure to online threats.